What is a Cyber Attack?
A Cyber attack uses malicious code to manipulate computer logic, code, or data that often results in data compromise, identity theft, or data theft. It is a deliberate attempt to exploit computer systems, accounts, networks, or companies that depend on technology.
Types of Cyber Attacks
Cyber attacks can happen in different ways. In most instances, they occur due to security holes created by people as a result of carelessness, human error, or employee turnover. In other cases, security holes in the network are attacked directly. Criminals are getting craftier with their malicious acts these days and following is the list of the most common types of cyber attacks and how you can prevent them.
Social Engineering:
Social Engineering is a type of cyber attack where criminals psychologically manipulate a person into revealing their private information such as their credit card details. Phishing and voice manipulation in a call are some significant examples.
- These kinds of cyber attacks can be prevented by developing one’s attention to detail. This can be done through training and educating themselves about such attacks.
Phishing Attack:
Phishing is the practice of sending malicious messages through telephone, emails, text messages, etc., composed to appear from reputed and familiar sources. They are sent by hackers to get victims to click on malicious links that give access to their private information.
- Getting scammed by a phishing link can be prevented by educating one’s self about secure links and being careful before entering any private data on suspicious links.
- Additionally, you could also get phishing detection tools like anti-virus software, email filters, etc. They provide a warning when something suspicious is detected.
Malware Attack:
Malware refers to malicious software such as worms, trojan horses, viruses, spyware, etc., to exploit companies by encrypting, misusing, destroying, or preventing access to their data. Once entered inside the network, malware can also produce extra harmful software throughout the system. It can hide within applications, and you may never come to know about it unless something dangerous happens.
- Malware attacks can be prevented by installing the latest and right anti-virus software and firewall setup. You should also make sure they are frequently updated.
Password Cracking Attack:
This type of attack is most usual in accounts that belong to celebrities and business enterprises. Hackers use brute force attacks and specialised software that can test numerous potential passwords to get access to these secure accounts.
- The only way to stay away from this attack is by having a long and random password that is harder for the software to guess.
- Keep your passwords safe. Set different passwords for different accounts and keep changing them on a regular basis.
Denial-of-Service Attack:
In this attack, hackers make a website unavailable to customers by overwhelming it with data and traffic until the site crashes. E-commerce websites are the main targets of this attack. Even though it does not have a direct financial loss to the website owners, this attack can lead to loss of sales until the website is fixed and goes live again.
- To prevent this attack, look out for unusual traffic patterns and monitor traffic reports of the website frequently. These can be your warning signs before the attack.
Man-in-the-Middle Attack:
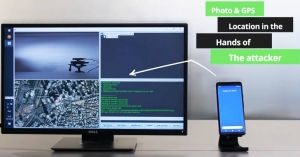
Generally, data flows consistently from users to the server and the backend. This flow gets interrupted when a man-in-the-middle (a hacker) steps in and obstructs the data being sent. The sad thing is that users would not even know that their data is being breached.
- To prevent becoming a victim of this attack, make sure you enter your information only on secure websites where the URL starts with HTTPS and not HTTP.
- Try not to visit a website when your browser prompts a security warning message.
- It would be best if you refrain from using an unprotected Wi-Fi connection.
In conclusion, ordinary users need to stay conscious during their time on the internet. Companies should have a qualified cyber security team to protect their information from such attacks. Employees should get training to spot possible cyber attacks.




 5. You can now select who can add you into groups among the three available options. “Everyone” where it would be no different from what it is now or “My contacts” where only the ones in your contacts can add or “My contacts except” where you can exclude people from your contacts especially those annoying and dodgy contacts.
5. You can now select who can add you into groups among the three available options. “Everyone” where it would be no different from what it is now or “My contacts” where only the ones in your contacts can add or “My contacts except” where you can exclude people from your contacts especially those annoying and dodgy contacts.
