In the digitally connected society, smartphones have become an extension to all of us. Advanced camera and video features are playing a massive role in this. Users can take out their phones to capture the moment with just a single click. However, it’s a double-edged sword. These mobiles are continuously collecting, storing and sharing the information without our knowledge making it a jackpot to the hackers.

For the better understanding of how the smartphone cameras may be opening up the users up to the privacy risks, the Checkmarx Security Research Team cracked into the applications that control the camera to identify the potential abuse scenarios. The team began with the Google Pixel 2xl and Google Pixel 3 reaching the Google Camera App, ultimately finding multiple concerning vulnerabilities coming from permission bypass issues. After digging deeper, they also found that the same vulnerabilities impact the camera app of the other smartphone vendors in the Android ecosystem, namely Samsung presenting hundreds of millions of significant users across the world.
Google & Samsung Camera Vulnerabilities
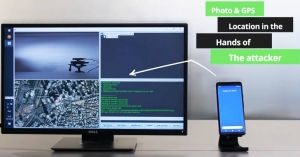
After the detailed analysis, the research team found that the Google Camera App can be attacked through a rogue application that has no permissions to do so. Additionally, specific attack scenarios also enable storage permission policies, giving them access to stored videos and photos. The GPS metadata embedded in the images to locate the user by taking the picture or the video and parsing into proper EXIF data. This technique is applied to the Samsung devices too.
In doing so, they determined a way to enable the rogue application to force the camera permissions even if the phone is locked and the screen is off. They could do the same even when the user was in the middle of the call.
Mitigation Recommended
For proper mitigation and best practice, please ensure that all the apps on your devices are updated.



Leave a Reply
Want to join the discussion?Feel free to contribute!